The Bitcoin Security Model
Bitcoin is first and foremost a social consensus network. Meaning, consensus between participants creates it’ behaviour. In the beginning it was just Satoshi. Then (as now) the Bitcoin protocol has existed without a formally defined security model. Its’ ability to survive without one is a testament to both its’ durability and simplicity.
In the interest of simplicity, (IMHO) Bitcoin’s security can be broken down into three major silos:
1. Bugs
2. Economics
3. Consensus
Yes, others certainly exist such as anonymity, mining centralization, and PoW alternatives (to name a few), but these are the major ones (again IMHO).
1. BUGS
Software bugs exist in all code, because humans (in this case – developers) are not perfect. Programmers often borrow legitimate code in shared libraries that can end up being malicious – here’s a couple of examples: JS NPM and RubyGems. Peer reviews and testing lower the risk of bugs. Yet security audits (or more precisely the lack there of) are by far the largest security gap with Bitcoin and its’ altcoin clones.
So the obvious follow-up question is… why? How can code responsible for billions of dollars for over a decade not consistently hedge this exposure? Don’t developers and those that fund them understand the risks? The easy answer is- good question, find out and if you hit a brick wall, ask them.
Bitcoin (BTC bugs) and the vast majority of altcoin bugs are discovered in an ad hoc manner because project leaders do not put their code against third party audits which is a well known way to deliver secure quality code. The Ethereum re-entry bug aka the June 2016 DAO hack is an obvious example. Even a basic checklist code review on a rolling basis is a sanity check that one doesn’t have to pay a lot for, but even that step seems to be lacking- see this list of hacks, glitches, and scams to get an idea.
The nearly $20Bn OneCoin ponzi didn’t even have code to review- talk about an easy audit!
Also, audits look for software best practices such as audit principles, standard operating procedures, and modular programming. The main point behind any audit esp. a security audit is trust. Trust that the code running the network is safe. Software teams (after all) are humans, and humans are not perfect.
2. ECONOMIC INCENTIVES
Bitcoin security is driven by economic incentives that govern good behavior (aka economic governance). Miners secure the network by enforcing consensus rules and are rewarded for the effort via block rewards, which will eventually be replaced by transaction fees. If those fees do not cover the cost of continual halving to eventually zero the network will not be able to survive in its’ current form anyway.
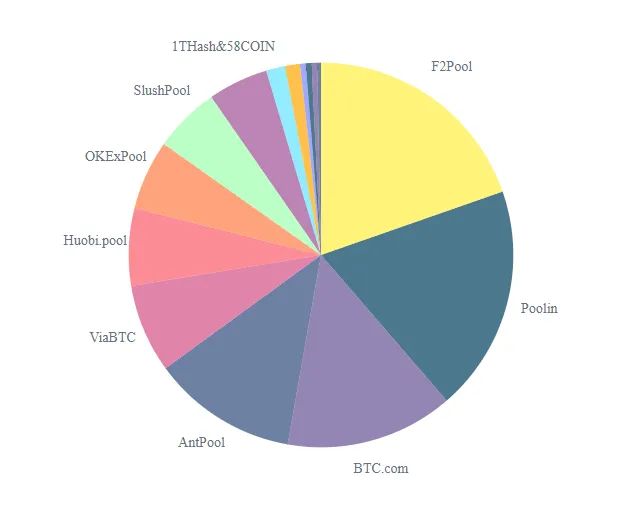
From 2009 to the present – trust in PoW consensus plus miner economic incentives are security essentials, yet what was lost is decentralization. ASIC mining put Bitcoin’s security into data centers making it more centralized which inadvertently increased the attack vector on the network because centralized mining simply makes a government’s ability to monitor it and/or shut it down a lot easier. Full stop.
However, a third pillar (i.e. external governance – or rules by which miners agree to abide by) would add significant weight to countering these concerns. Mining is economic risk for the miner, their competition, and end-users. Why? Because mining is expensive competition for block rewards, but no system built by humans is flawless. Mining is also a protection racket since the most severe attacks only they can launch. For example….
Example: 51% Attack
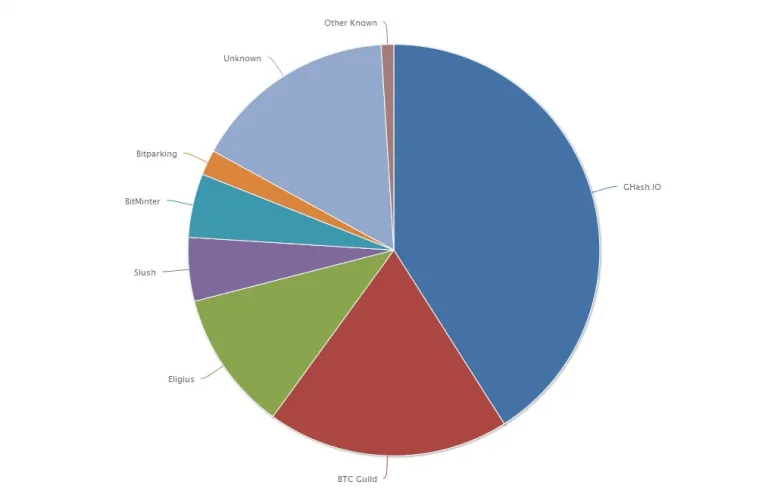
When a miner or group of miners owns a majority of the computing power (aka hash rate) the network is open to what is known generically as a 51% attack – this advantage can be used to fork the legitimate blockchain and commit fraud (via double spending).
As discussed here, this attack has a lot of historical precedents. Bitcoin itself was exposed to this attack in January 2014 when the Ghash.io mining pool, began approaching the 50% limit. This was resolved when miners left Ghash.io for smaller pools, and the pool decided to stop accepting new miners.
Today,…
3. CONSENSUS & BEHAVIOR:
Per the authors of “Research Perspectives and Challenges for Bitcoin and Cryptocurrencies” the following properties are essential to understanding security via block behavior and consensus:
- Liveness: New blocks will continue to be added and valid transactions with appropriate fees will be included in the blockchain within a reasonable amount of time.
- Correctness: All blocks in the chain with the most cumulative proof of work will only include valid transactions.
- Fairness: A miner with X% of the network’s total computational power will mine approximately X% of blocks.
- Exponential convergence: The probability of a fork of depth n is O(2−n). This gives users high confidence that a simple “k confirmations” rule will ensure their transactions are settled permanently.
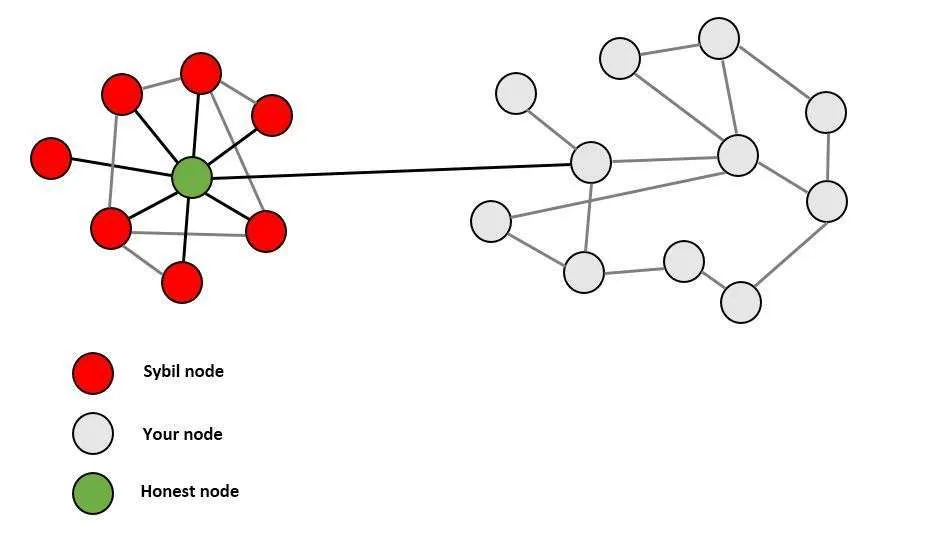
- Eventual Consensus: At any time, all compliant nodes agree upon a prefix of what will become the eventual “true” blockchain. An honest chain is preserved via sybil resistance…
Example: Sybil Resistance
Proof of work helps protect the integrity of the network as new peers join they only need to connect to a single honest peer in order to find the honest chain. This is also known as Sybil resistance- “which means that it’s not possible for someone to launch an attack against a node by creating many dishonest peers that feed it false information.” J. Lopp (Nov 2016)
Example: Privacy
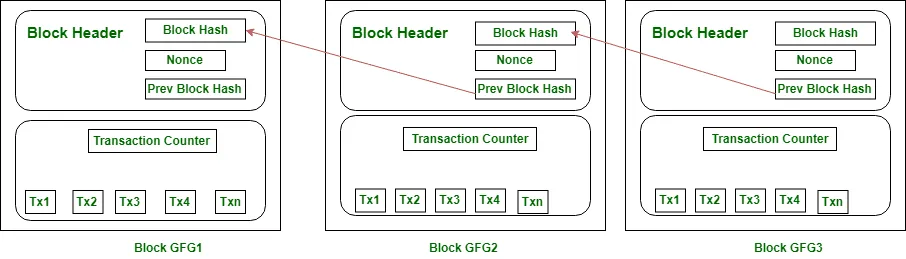
Bitcoin’s transactions create a distributed ledger (aka blockchain) giving all participants a record of all transaction data. To that end the SHA-256 hash algorithm is needed for:
* Proof-of-Work and
* Transaction verification
The blockchain with the most cumulative proof of work is considered the valid chain and the one that the entire network refers to when verifying transactions. Bitcoins are considered spent once a transaction has been verified.
The above falls apart if SHA-256 was compromised. It just so happens that it was designed by the NSA. To be fair no third party has ever found an issue with SHA-256, but the larger (and real) issue is privacy.
When you use Bitcoin your transaction can be tracked. Under normal circumstances money as cash is private, but Bitcoin (and many altcoins) are not. If digital money cannot mime fiat in this regard there will be giant adoption issues moving to a pure cashless society. Data generated by a company or individual is sovereign to that company or individual – the Bitcoin protocol derives its’ strength from recorded data on the blockchain, thus it cannot escape this Catch-22 without that ugly word – compromise – because companies and users need privacy and governments need visibility to enforce regulation and levy taxes.
This is a zero sum game folks – either everyone (literally) can see everything or not. It’s just that simple. No one can have their cake and eat it at this level. If everyone can see everything from a coffee purchase to the NSAs budget maybe simple transparency is the final (and only) arrangement here.
Thus, Ben Franklin was right again…. “Tricks and treachery are the practice of fools, that don’t have brains enough to be honest.”
RESOURCES:
Please see these links for more insight and security education:
Below is a running list of community vulnerability issues, contacts, and open disclosures.
Blockchain Security Contacts List: Trail of Bits (2018)
Top Picture from https://wallpapercave.com/ancient-greek-warriors-wallpaper
| https://99bitcoins.com/how-to-kill-bitcoin/
China Mining: WSJ: https://www.wsj.com/articles/china-quietly-orders-closing-of-bitcoin-mining-operations-1515594021
| https://medium.com/coinmonks/bitcoin-security-in-one-chart-694ee3ed8c2d